
SSL certificate revocation gotchas
As you may have heard, Let's Encrypt revoked several certificates today that were issued through a faulty process. Read on for the details, and on how to identify the revoked certificates themselves.
CAA and a faulty process
Certification Authority Authorization or CAA for short is a DNS entry that can help domain owners announce (and limit) which Certification Authority is authorized to issue certificates for these domains. Since September 2017, all Certificate Authorities that issue public certificates are required to check the CAA record before they do so. If for example the CAA record for one domain indicated Thawte, then only Thawte is authorized to issue certificates for this domain and all other Certificate Authorities must refuse to do so.
Let's Encrypt had a faulty process that did not check for the CAA record before issuing a certificate; that resulted in Let's Encrypt having to revoke more than 3 million certificates. This faulty process may have led to a huge opportunity to phishers, as they could have requested certificates for subdomains, issued by Let's encrypt, while not being authorized.
Browsers and OCSP
You may wonder, how does one know that the certificate is revoked? The simple answer is that the browser will tell you.
This is what you see on Chrome:
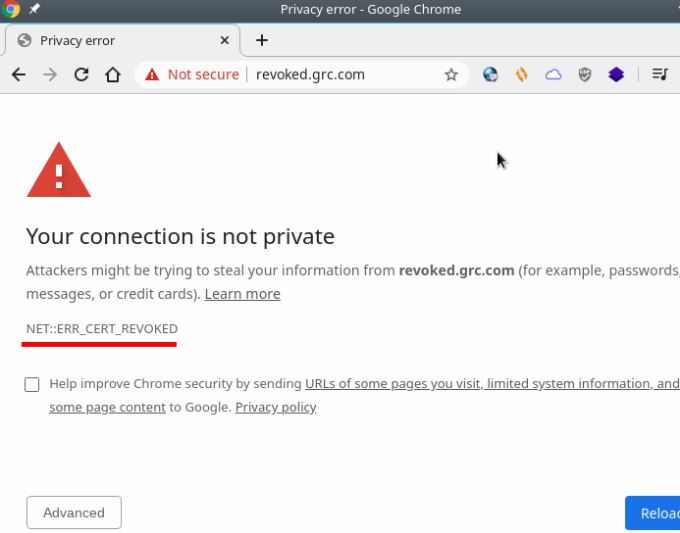
This is what you see on Firefox:
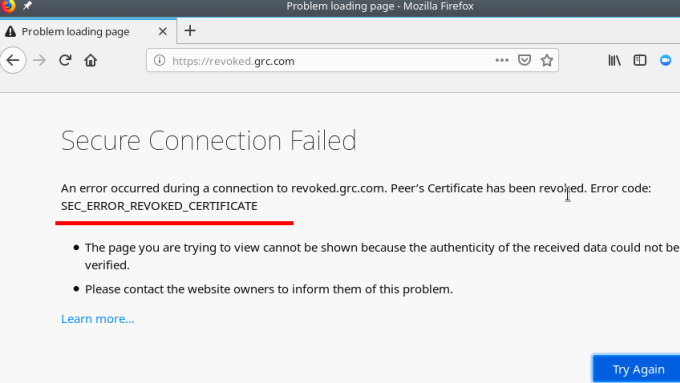 And how does the browser know? Well, there is one thing called Online Certificate Status Protocol or OCSP for short and it does exactly that. Furthermore, most web servers implement OCSP Stapling which means that the server itself will tell the browser that the certificate is revoked. If the browser doesn't receive an OCSP package from the server, it will go and ask on its own.
And how does the browser know? Well, there is one thing called Online Certificate Status Protocol or OCSP for short and it does exactly that. Furthermore, most web servers implement OCSP Stapling which means that the server itself will tell the browser that the certificate is revoked. If the browser doesn't receive an OCSP package from the server, it will go and ask on its own.
Certificates in 2020
The certificates and overall Public Key Infrastructure are of huge importance in 2020. Certificates are there to provide Trust and Identification and any flaw in the certificate management, such as this one, may have catastrophic security impact. This doesn't say much about Let's Encrypt, a pioneer in Certificate Management. They are not the only, definitely not the first and won't be the last Certificate Authority to have a certificates related incident.
In the past many Certificate Authorities failed to check ownership (one of the main reasons that led to CAA record) or failed to protect keys appropriately. So us, as individuals, have to always be vigilant.